For personal mobile devices or even organization-owned devices that aren’t configured for supervision, users can use the Company Portal app to self-enroll (as a personal device) and then download the MDE app from inside Company Portal or just go straight to the App Store and download MDE. It will require the user to sign in, at which point they’ll get the settings you’ve configured for the organization.
You can also create a deployment profile that manages the settings for users who are either logged in through Company Portal or who just download and deploy the app to their individual devices.
Exam Tip
Microsoft identifies targeting devices for assignment, as opposed to users. Policies applied to users aren’t processed until the user logs in.
Onboarding Android Devices
Android devices support both user-based installations as well as administrator-initiated installations for Intune-enrolled devices. MDE for Android, like MDE for iOS, also supports managing settings through Intune.
Like iOS, Android devices have several configuration modes and features for managed or Intune-enrolled devices. Android has the legacy Device Administrator and modern Android Enterprise modes. In addition, personally owned and corporate-owned devices can be managed with a work profile.
And, for devices that will not be enrolled and using Intune as an MDM platform, MDE settings can still be configured to send risk signals via an app protection policy.
Note
The MS-102 exam doesn’t focus on Intune configuration and deployment for MDM and provisioning. Configuring for Android Enterprise is outside the scope of the MS-102 exam.
In the upcoming sections, you’ll look at configuring Android, focusing on bring-your-own-device (BYOD) and enterprise enrollment scenarios.
Bring Your Own Device
To configure an onboarding package for Intune-enrolled BYOD Android devices, follow these steps:
- Navigate to the Intune admin center (https://endpoint.microsoft.com).
- Select Apps from the navigation menu, and then select Android apps from the middle pane.
- In the details pane, click Add.
- On the Select app type flyout, under App type, select Android store app. See Figure 9.27:
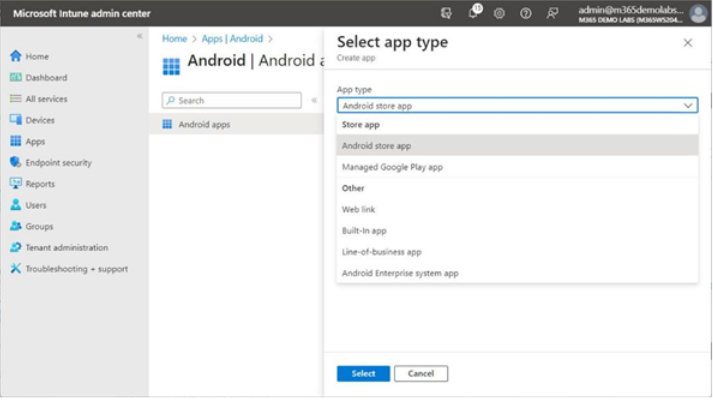
Figure 9.27 – Selecting the Android store app type
- Click Select.
- On the App information tab, populate the required fields of Name, Description, and Publisher.
- In the Appstore URL field, enter the URL for the Microsoft Defender app in the Google Play
Store: https://play.google.com/store/apps/details?id=com.microsoft.
scmx. See Figure 9.28:
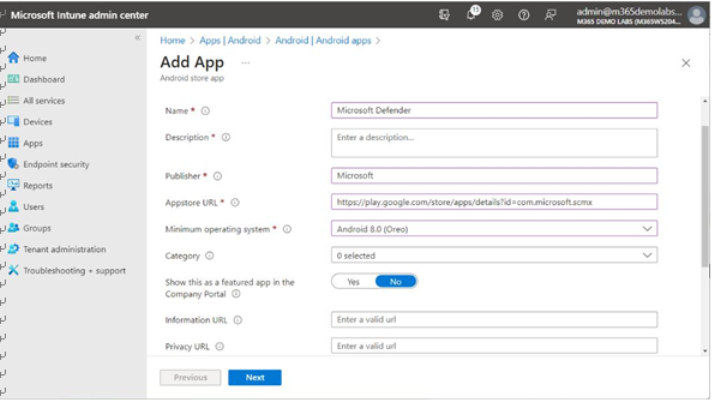
Figure 9.28 – App information tab
- Click Next.
- On the Assignments tab, under Required, choose to add groups containing devices that will be in scope for the policy.
- On the Review + create tab, verify the settings and click Create.
Once the MDE app has been deployed, the user will need to launch the app and sign in to it.
