Once the Security baselines assessment | Profiles tab has been updated, you can check your organization’s compliance against that profile. On the Profiles tab, after the profile data has been updated, you will see how the devices in the baseline score against the baseline assessment and compliance settings chosen in the profile. Figure 9.41 displays a high-level overview:
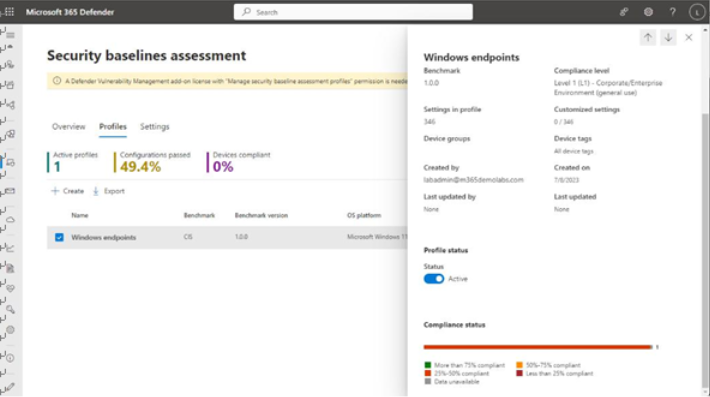
Figure 9.41 – Profile assessment
You can select the name of the profile to view its details page, which will show information regarding compliance against the selected policy configurations as well as each individual in-scope device’s rating. The Configurations tab shows each selected profile configuration ID. You can drill further down by selecting a particular configuration ID to see the supporting details, such as the rationale, what local device configuration setting is being validated, the configuration category, and steps to bring an item into compliance.
Figure 9.42, the Devices tab, shows individual devices that are in scope for the profile and their compliance against the profile:
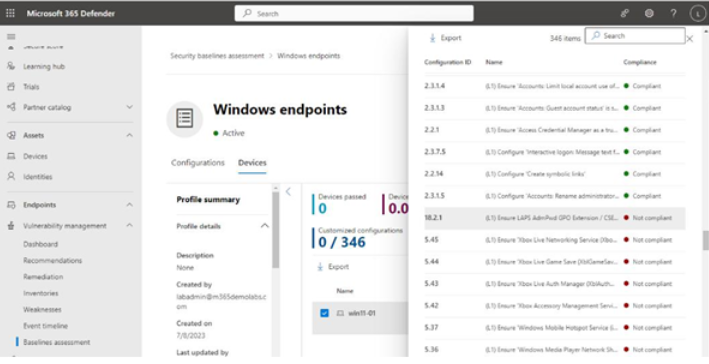
Figure 9.42 – Viewing an individual device’s compliance against a baseline profile
This detailed view allows you to see exactly which device policy settings need to be adjusted to become compliant with the profile.
Creating and Managing Exceptions
As with other features in Vulnerability Management, you may have devices that need to be excluded from being included in a particular policy or configuration item for various reasons—such as a policy item being mitigated by a third-party piece of software or alternate control. To configure an exception for a device, follow these steps:
- Navigate to the Microsoft 365 Defender portal (https://security.microsoft. com), expand Vulnerability management, select Baselines assessment, and then choose the Exceptions tab.
- Select Create.
- Add the details of the justification, including the reason and duration. Click Next.
- On the Configuration scope page, choose the software, benchmark, and compliance level where the policy item(s) to be excepted occur and click Next.
- On the Select configurations page, select the configuration IDs to be included in the exception. Click Next.
- On the Devices page, select the devices to be accepted from the configuration. Click Next.
- Click Submit.
Exceptions are applied on a per-configuration ID, per-device basis. That is, if a device appears in multiple profiles, is in scope, and is tracking against the same baseline and compliance configuration ID, it will be excluded from reporting for all of the profiles.
As you can see, all of it items in the Threat Management area are connected—each giving you a different view into various pieces of your organization’s infrastructure and assets, linking back to the same devices. This helps you get a holistic view of impacted devices, applications, data, and users as well as the relative risk levels that each item presents.
Now that you’re familiar with some of the vulnerability management pages, let’s switch gears to threat and risk management.
