When threats are detected, Microsoft 365 Defender will create incidents and alerts. You can monitor and manage alerts and incidents from the Microsoft 365 Defender portal.
Tip
Microsoft 365 Defender provides sample files that you can use to understand how to detect and process risks. The examples in this section were generated using the automated investigation (backdoor) simulation, available for download at https://security.microsoft.com/ tutorials/simulations. We recommend deploying a simulation to a test environment so you can more deeply understand the vulnerability management experience and interface.
Microsoft Defender 365 has some basic terminology you’ll need to understand in order to be successful—both on the MS-102 exam as well as managing security operations:
• Alert: A detected event that generates a notification. In the context of Microsoft 365 Defender, an alert is specific to some sort of suspicious or threat-like activity. An alert may be generated by a single event (such as the detection of malware) or a series of similar, related events (such as multiple bad password attempts from multiple geographic locations or malicious script activity).
• Incident: A group of correlated events that are aggregated together. Incidents are used to provide context and timelines for attacks.
• Alerts queue: Shows the alerts across various Microsoft solution areas, including Defender for Endpoint, Defender for Office 365, Defender for Cloud Apps, and Defender for Identity.
• Attack story: A multifaceted way of displaying an incident’s corresponding alerts and events. Stories can have timelines, graphs, and other data objects to represent how a threat or threat actor is moving across your organization—whether it’s contained on a single endpoint, what processes were invoked, what other endpoints were contacted, what content was downloaded, and more.
• Indicators of compromise (IOCs): Signals used to generate alerts. An IOC might be a particular file or file hash, an IP address, a device, an identity, a URL, or any other piece of information used in determining whether something is a threat or risk.
Incidents and alerts are depicted in the Microsoft 365 Defender interface inFigure 9.43:
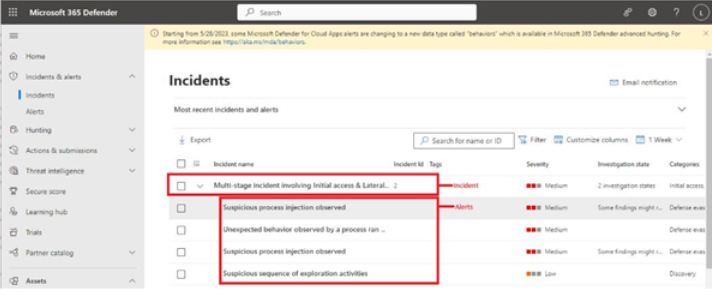
Figure 9.43 – Microsoft 365 Defender incidents and alerts
The alerts queue is displayed by selecting Alerts under Incidents & alerts. Like other pages in vulnerability management, you can filter the alerts by various criteria, including Severity, Status, Categories, and which service sources were responsible for generating the alert.
When working with security incidents, you may find it best to use a standard approach to triaging. A helpful approach is to examine the current incidents and prioritize them according to Severity (the risk level assigned by Microsoft 365 Defender) andImpact (a description of how widespread or business-affecting an issue might be, the number of affected users or applications, or the types of alerts).
Investigate
Once an incident has been generated, you can begin investigating all of the related alerts. Like the other pieces in Vulnerability management, each file, process, device, and activity is linked to the related items.
