This page lists current threats in the organization along with corresponding security recommendations.
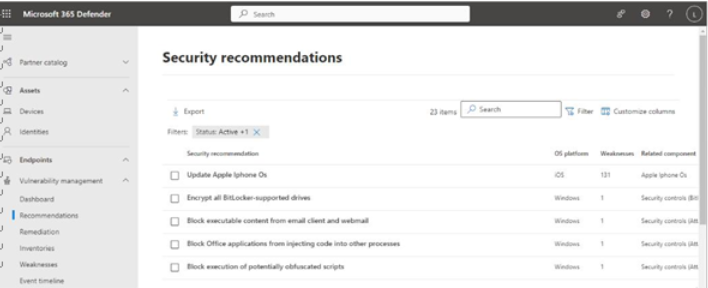
Figure 9.32 – Recommendations page
Selecting an item displays a flyout with information and activities. From here, you can select individual security recommendations to view detailed information about devices or other areas that might be exposed, relevant items tracked in the Common Vulnerabilities and Exposures (CVE) system, and possible remediation measures.
You can select Request remediation (see Figure 9.33) to start the process of creating a remediation assignment or task:
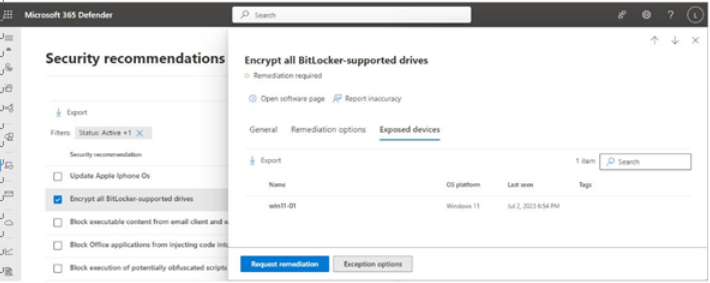
Figure 9.33 – Request remediation
When creating a remediation assignment, you have the option of just creating a tracked remediation item or creating a task in the Intune admin center.
You can also create an exception to acknowledge risk and alternate mitigations, along with setting an end date for the exception to expire (up to 1 year). Exceptions are displayed and tracked along with remediation assignments.
Items marked for exception still show up as open vulnerabilities in Threat Management. You can prevent devices from being included in reporting and management pages by excluding them from the view. You might do this, for example, if you’ve offboarded the device or it’s a duplicate item. To do this, navigate to Microsoft 365 Defender| Assets | Devices, expand the … menu at the top of the device page, and select Exclude. See Figure 9.34:
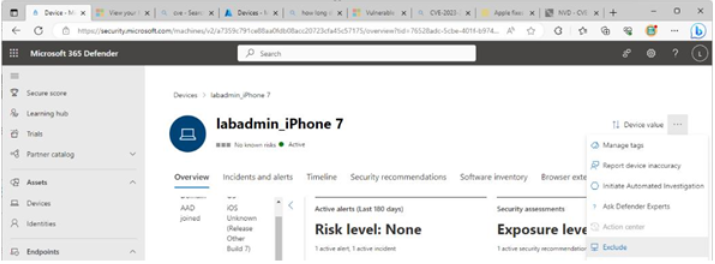
Figure 9.34 – Excluding a device from Threat Management
Excluding a device will result in its vulnerabilities not being reported to Threat Management. If MDE is still active on an excluded device, however, it continues to be protected from malicious on-device activity through the network filtering component.
Remediation
The Remediation page lists any currently assigned or started remediations along with their current status. Remediation actions might include stopping or disabling processes, running a script, resetting a password, or sending files to quarantine.
This page also allows you to manage any existing exceptions. Selecting an item displays a flyout with details and allows you to sekect Mark as completed, updating the status of the item (see Figure 9.35):
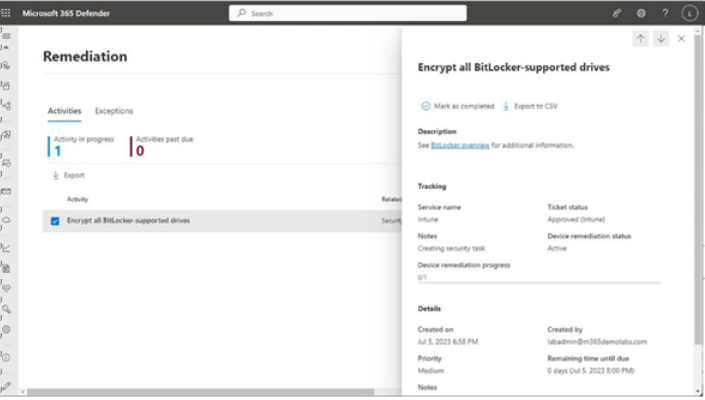
Figure 9.35 – Remediation page
Items marked as completed will continue to show up in the dashboard for 180 days. You can filter items on the Remediation page using any combination of the selectable attributes shown in Table 9.3:
Table 9.3 – Filter parameters
Next, you’ll look at the threat vulnerability management view of the asset inventory.
