MDE can inspect network traffic and report back to the Microsoft 365 Defender portal. Use the following steps to create a configuration profile that allows the network extension to perform this activity:
- Download the configuration file from https://raw.githubusercontent.com/ microsoft/mdatp-xplat/master/macos/mobileconfig/profiles/ netfilter.mobileconfig and save it to the temporary location where you stored the macOS onboarding package.
- On the Devices | Configuration profiles page in the Intune admin center (https://endpoint.microsoft.com), click Create profile.
- On the Create a profile flyout, under Platform, select macOS. Under Profile type, select Templates and then choose Custom. Click Next.
- On the Basics tab, enter a name and description and click Next.
- On the Configuration settings tab, enter a custom configuration profile name to identify this configuration.
- Under Deployment channel, select Device channel.
- Under Configuration profile name, click the folder icon and browse to the folder containing the downloaded configuration file. Select the netfilter.mobileconfig file and click Next.
- On the Assignments tab, under Included Groups, choose to add groups containing devices that will be in-scope for the policy.
- On the Review + create tab, verify the settings and click Create.
Next, you’ll create a configuration profile to manage device notifications.
Notifications Configuration Profile
This configuration profile is necessary to allow Intune and MDE to display notifications in the macOS interface. To create the configuration profile, follow these steps:
- Download the configuration file, https://raw.githubusercontent.com/microsoft/ mdatp-xplat/master/macos/mobileconfig/profiles/notif.mobileconfig, and save it to the temporary location where you stored the macOS onboarding package.
- On the Devices | Configuration profiles page in the Intune admin center (https://endpoint.microsoft.com), click Create profile.
- On the Create a profile flyout, under Platform, select macOS. Under Profile type, select Templates and then choose Custom. Click Next.
- On the Basics tab, enter a name and description and click Next.
- On the Configuration settings tab, enter a custom configuration profile name to identify this configuration.
- Under Deployment channel, select Device channel.
- Under Configuration profile name, click the folder icon and browse to the folder containing the downloaded configuration file. Select the notif.mobileconfig file and click Next.
- On the Assignments tab, under Included Groups, choose to add groups containing devices that will be in scope for the policy.
- On the Review + create tab, verify the settings and click Create.
Finally, you’ll create the configuration profile to enable MDE to run in the background.
Background Services Configuration Profile
Starting with macOS 13 (Ventura), the operating system contains a new privacy design that prevents applications from running in the background (in daemon mode) without explicit consent. This configuration profile enables MDE to run as a background process. To create the configuration profile, follow these steps:
- Download the configuration file, https://raw.githubusercontent.com/microsoft/ mdatp-xplat/master/macos/mobileconfig/profiles/background_ services.mobileconfig, and save it to the temporary location where you stored the macOS onboarding package.
- On the Devices | Configuration profiles page in the Intune admin center (https://endpoint.microsoft.com), click Create profile.
- On the Create a profile flyout, under Platform, select macOS. Under Profile type, select Templates and then choose Custom. Click Next.
- On the Basics tab, enter a name and description and click Next.
- On the Configuration settings tab, enter a custom configuration profile name to identify this configuration.
- Under Deployment channel, select Device channel.
- Under Configuration profile name, click the folder icon and browse to the folder containing the downloaded configuration file. Select the background_services.mobileconfig file and click Next.
- On the Assignments tab, under Included Groups, choose to add groups containing devices that will be in scope for the policy.
- On the Review + create tab, verify the settings and click Create.
As new macOS devices are enrolled in Intune, the MDE deployment package will automatically be sent to them. The Intune admin center displayed in Figure 9.24 shows a macOS device that has been automatically configured with MDE:
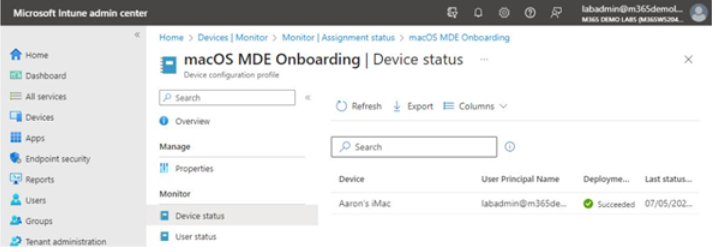
Figure 9.24 – macOS enrolled in Intune
Figure 9.25 shows a newly onboarded macOS device that has a FileVault encryption policy configured.
As it is a policy requirement, the user must click Enable Now to be able to log in.
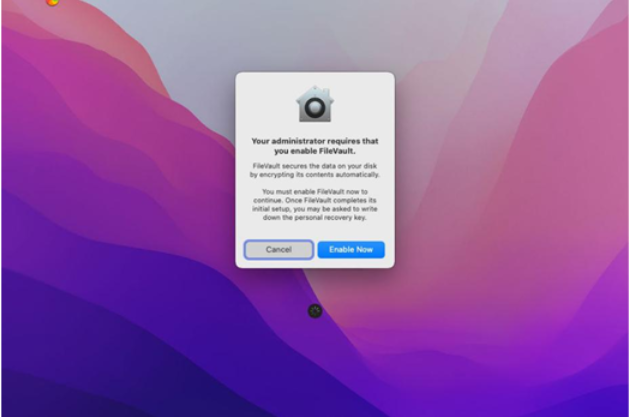
Figure 9.25 – macOS with FileVault encryption policy enabled
Next, you’ll shift focus to mobile devices.
