The Investigations tab is used to track the triggering alerts for the incident. After selecting an alert to view its details, you can select Open investigation page to get a deep insight into the event, as shown in Figure 9.47:
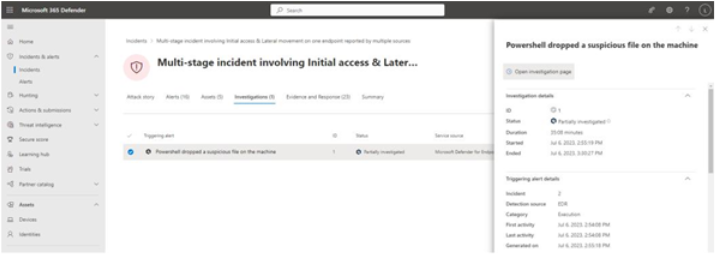
Figure 9.47 – Triggering alert investigation
The Investigations page for an alert shows details much like the Attack story tab, highlighting the correlated alerts and entities that were analyzed. See Figure 9.48:
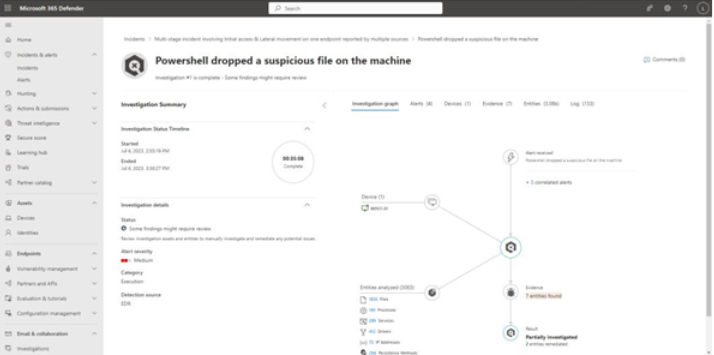
Figure 9.48 – Investigations page
You can further investigate the items by clicking on the relevant tabs. While many of the tabs are familiar, three tabs stand out on this page: Evidence, Entities, and Log.
The Evidence tab provides details about specific files that were detected and processes that were executed. You can investigate these items to learn more about automated actions that Defender has taken, view additional details about the file, or even start a threat hunt in your organization based on the item. See Figure 9.49:
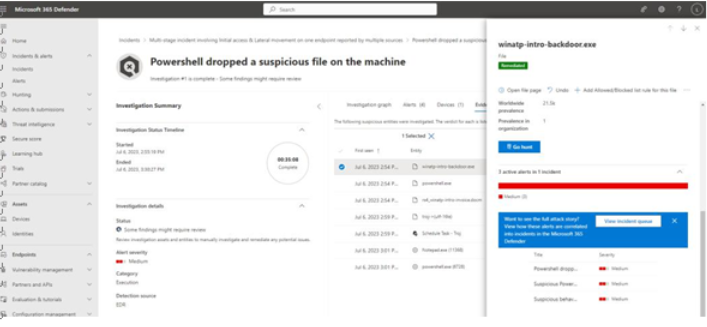
Figure 9.49 – Evidence details
The Entities tab shows all of the items that were scanned or included as part of the investigation, including Files, Processes, Services, Drivers, and IP Addresses. Additionally, the Entities tab also shows Persistence Methods—a view that reports the ways that a threat may attempt to hide itself or evade detection and removal and whether Defender located the threat at any of those locations.
The Log tab shows the activities that Defender has taken automatically, such as locating files, listing network connections, listing active services and processes, and taking an inventory of the device’s memory.
Evidence and Response
The Evidence and Response tab for the incident shows much of the same information as the Evidence tab in an investigation—the main difference being the absence of the Persistence Methods information from the Evidence tab.
Just like the Evidence tab in an investigation, you can select individual items to dive deeper into each one. Depending on the context and type of evidence, you may be able to download files, examine IP address ownership, look at file header information, quarantine files, or submit the evidence (files or other captured content) for analysis. See Figure 9.50:
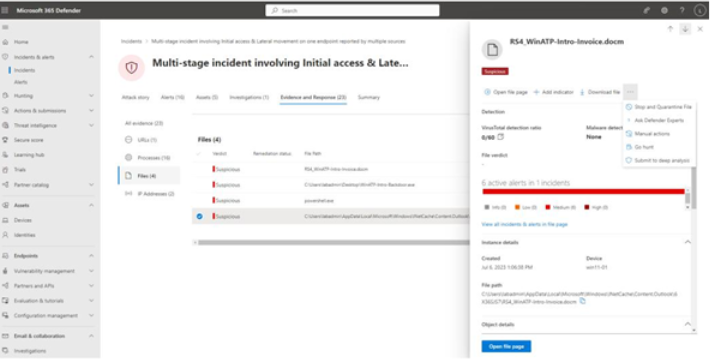
Figure 9.50 – Incident evidence
Other options include invoking help from Microsoft Defender Threat Experts (available as a separate subscription) or using the item to pivot into threat hunting (using the Go hunt option).
Respond
Once you have begun analyzing and working on an incident, you may have several options on how to respond.
Taking Actions
Depending on the Microsoft 365 Defender subscription, you may have different options for automated or manual remediation. The types of actions Defender can take are generally divided into two categories: actions that can be performed on devices and actions that can be performed on files.
Let’s look into each of those areas.
