The Inventories page catalogs discovered items, as shown in Figure 9.36:
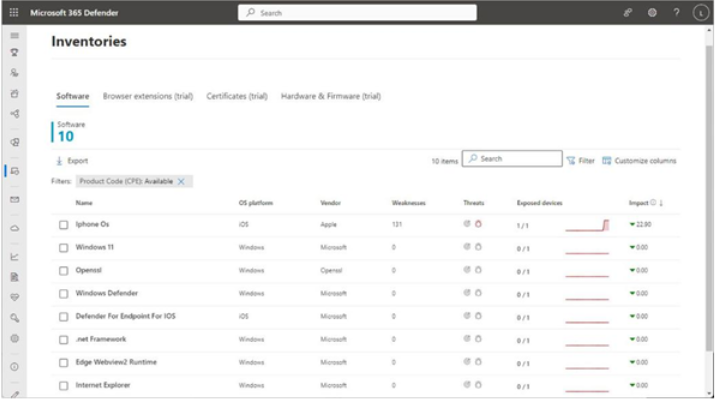
Figure 9.36 – Inventories page
Each tab displays different categories of information. You must have a Plan 2 license, however, to see data on the Browser extensions, Certificates, and Hardware & Firmware tabs.
The Software tab is used to show a high-level overview of software (both components and applications) identified in your organization, along with information about the platform, the number of known threats across all the devices with the associated software, the number of exposed devices in relationship to the number of total devices, and the relative impact on your exposure and Secure Score.
The Browser extensions tab displays information gathered about installed browser extensions along with the browser, the operating system the browser is running on, the highest risk level generated by the extension based on what access or sites the extension requested, and the version information.
The Certificates tab displays information regarding certificates that are potentially vulnerable. Certificates are identified for risk based on whether they have expired or will expire within 60 days, as well as potential vulnerabilities due to key length or algorithm and self-signed certificates.
The Hardware & Firmware tab displays inventoried information regarding what types of devices have been discovered (laptop, desktop, and servers), what types of processors are identified, and which BIOS or firmware levels are in place. Vulnerability and risk information is available for Lenovo, Dell, and HP models only.
You can drill down into items on each of the pages, eventually arriving at a device’s inventory page. A device’s inventory page displays all of the connected risks, vulnerabilities, incidents, and other details associated with a device. Depending on the type of device, you may see information about missing updates, security baseline information, and other policies applied to it. You also have the ability to add your own categorization to the device based on its device value.
About Device Value
Device value is a subjective assignment of value. By default, all devices are configured with a value of Normal. You can adjust a device’s value (Low, Normal, and High) based on any number of factors you determine are important. For example, you may want to categorize an executive’s laptop or the server containing payroll data with a High value, while a shared computer in a lab might be downgraded to a Low value. The categorization value impacts your organization’s overall exposure score (High-value devices have more impact than Normal-value devices, and Normal-value devices have more impact than Low-value devices).
Weaknesses
Like other pages in Vulnerability Management, the Weaknesses page categorizes threats to your environment. This page, however, approaches it from a different perspective by displaying the combined
list of unique vulnerabilities across all devices and then highlights the important data points such as which are exploitable, zero-day exploits, and whether updates are available. See Figure 9.37:
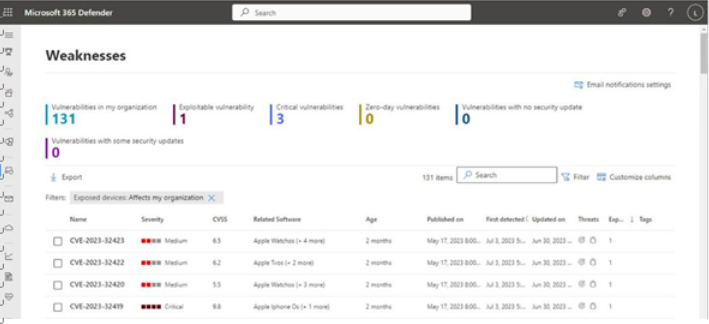
Figure 9.37 – Weaknesses page
You can sort the vulnerabilities by a variety of properties, including software name, CVE item ID, severity, and the number of exposed devices. Selecting a vulnerability item surfaces a flyout with a link to the corresponding item on the Recommendations page.
