You can also configure MDE as an enterprise-managed app for Android devices. These settings are designed for devices with a work profile and assume you have already completed the Intune connection to the Google Play Store with a Google Play account. To configure MDE as an enterprise-managed app, follow these steps:
- Navigate to the Intune admin center (https://endpoint.microsoft.com).
- Select Apps from the navigation menu, and then select Android apps from the middle pane.
- In the details pane, click Add.
- On the Select app type flyout, under App type, select Managed Google Play app.
- In the search bar, enter Microsoft Defender to locate the MDE app. See Figure 9.29:
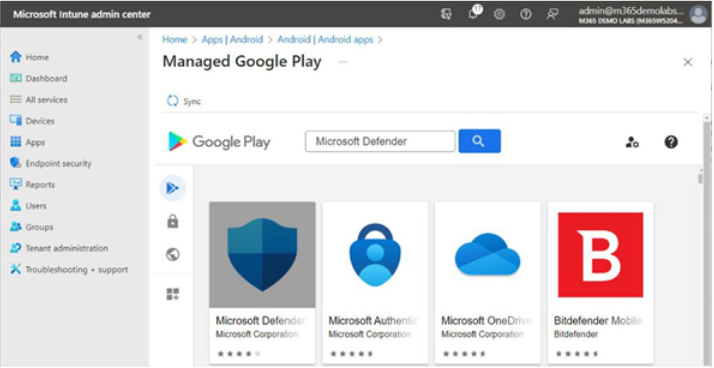
Figure 9.29 – Locating the Microsoft Defender app
- Select the Microsoft Defender app.
- In the details pane, click Approve.
- On the permissions dialog, confirm the allowed permissions and click Approve.
- On the Approval Settings tab, select Keep approved when app requests new permissions and click Done.
- At the top of the details pane, click the Sync button to update the app configuration policy.
- After the sync has completed, you should see the Microsoft Defender app listed as a managed
Google Play Store app. See Figure 9.30:
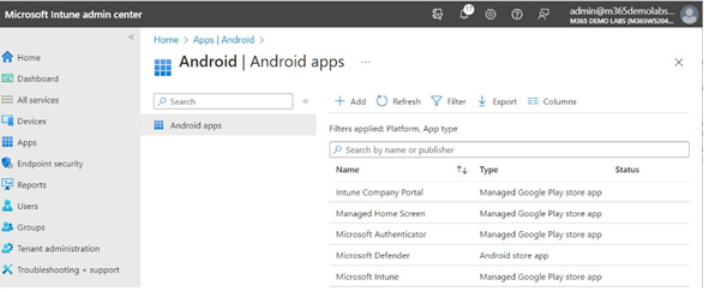
Figure 9.30 – Managed Google Play Store apps
You can manage additional settings for the app by creating an app configuration policy.
Further reading
For more information on mobile application management (MAM), see https://learn. microsoft.com/en-us/mem/intune/apps/app-management#mobile-application-management-mam-basics.
Next, you’ll learn how to detect and manage endpoint vulnerabilities.
Reviewing and Responding to Endpoint Vulnerabilities
Microsoft 365 Defender, as part of Plan 2, includes theVulnerability Management feature. Vulnerability management, in the context of the environment’s threat landscape, means the following:
• Asset inventory and discovery: Cataloging of assets (such as identities, certificates, browser extensions, network shares, devices, and applications) across the organization
• Vulnerability and configuration assessment: Reviewing the asset inventory for exposure to known or emerging threats and reporting on it
• Risk-based intelligent prioritization: Reviewing the assessed threats and categorizing them based on exposure
• Remediation and tracking: Taking and monitoring actions to reduce or resolve the risks, such as installing software updates, uninstalling applications or unwanted programs, or making device configuration changes
The Vulnerability Management dashboard (https://security.microsoft.com/ tvm_dashboard), shown in Figure 9.31, offers a high-level view of organizational assets, risks, and recommendations:
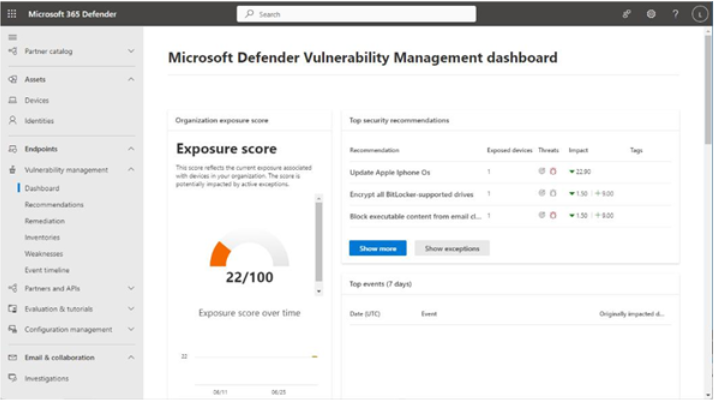
Figure 9.31 – Vulnerability Management dashboard
From here, you can select cards that display statistics or graphs of the various risk areas. You can also use the navigation menu to move between the different vulnerability management pages:
• Recommendations
• Remediation
• Inventories
• Weaknesses
• Event timeline
Let’s look at each of these areas.
