You can also create an EDR policy to enable MDE settings. To configure an EDR policy, use the following procedure:
- Navigate to the Intune admin center (https://intune.microsoft.com).
- Select Endpoint security, and then under Manage in the middle pane, select Endpoint detection and response.
- Click Create policy. See Figure 9.16:
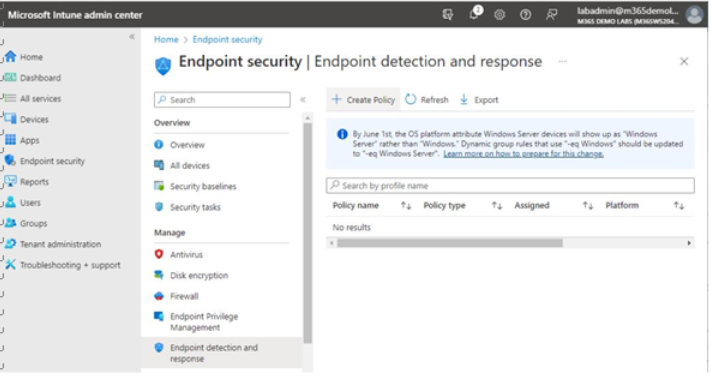
Figure 9.16 – Creating an EDR policy
- Under Platform, select Windows 10, Windows 11, and Windows Server.
- Under Profile, select Endpoint detection and response and click Create.
- On the Basics tab, enter a name and a description, and then click Next.
- On the Configuration settings tab, under Microsoft Defender for Endpoint, select a Microsoft Defender for Endpoint client configuration package type setting. You can select from Auto from connector, Onboard, Offboard, and Not configured. For integrated deployments, Microsoft recommends choosingAuto from connector.
- Click Next.
- On the Scope tags tab, assign any scope tags for your environment and click Next.
- On the Assignments tab, under Included groups, select what will be in scope for this policy. For the purpose of this configuration, you can select Add all devices and click Next.
- Click Create.
After Intune has refreshed the policy against the devices in scope, the onboarding package will be deployed.
You can view your devices’ statuses in the Microsoft 365 Defender admin center underDevices, as shown in Figure 9.17:
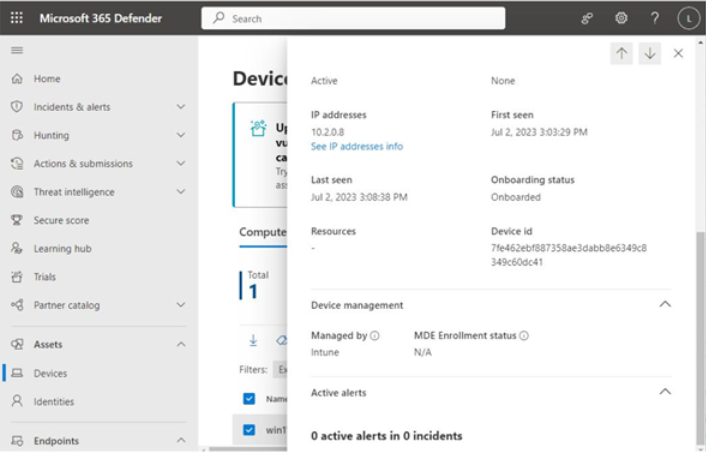
Figure 9.17 – Microsoft 365 Defender admin center device onboarding status
If you’ve configured and deployed MDE through both the Intune integration as well as an EDR policy for the same devices, you may end up with a conflict. While it’s not a critical issue per se, you may get error conditions displayed, as shown in Figure 9.18:
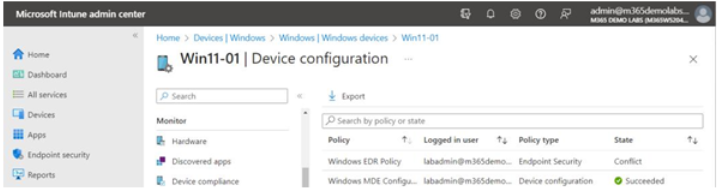
Figure 9.18 – Defender for Endpoint policy conflict
Microsoft recommends you only use one method for deploying or configuring MDE per device.
Other Onboarding Alternatives
In addition to using Intune’s device configuration profile to onboard devices, you can also onboard using the following methods:
• Group policy: https://learn.microsoft.com/en-us/microsoft-365/ security/defender-endpoint/configure-endpoints-gp
• Local script: https://learn.microsoft.com/en-us/microsoft-365/security/ defender-endpoint/configure-endpoints-script
Whichever method you choose to use, after you have successfully onboarded your first device, you can check to see that Defender for Endpoint recognizes that the first device has been onboarded. In addition to the Devices page shown previously in Figure 9.17, you can also check to make sure your first device has been onboarded under the Settings | Endpoints | Onboarding section of the Microsoft 365 Defender admin center, as shown in Figure 9.19. First device onboarded (as well as view directions for other onboarding mechanisms) will display Completed if your configuration has been successful.
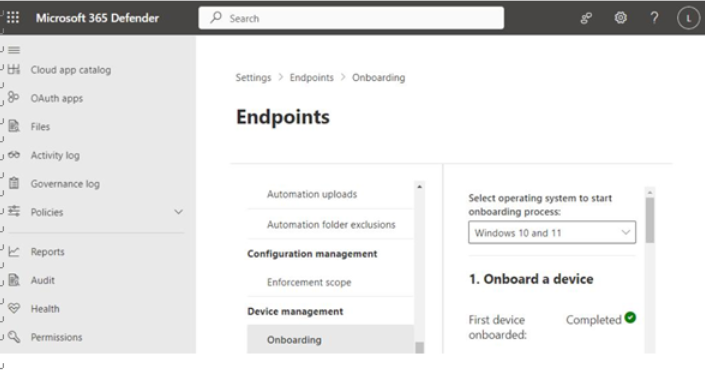
Figure 9.19 – Reviewing endpoint onboarding status
Further Reading
Microsoft provides an excellent reference on all the avenues available for onboarding devices in the online documentation as well. See https://github.com/MicrosoftDocs/microsoft-365docs/raw/public/microsoft-365/security/defender-endpoint/downloads/mdatp-deployment-strategy.pdf for the supported deployment methods.
