Once you have identified devices that are impacted, you can choose how to respond. See Figure 9.51 for the potential actions:
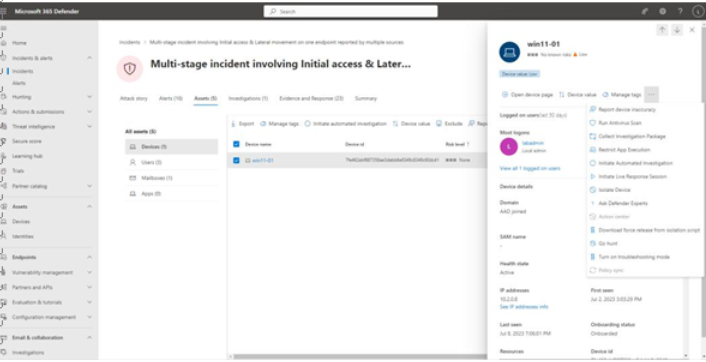
Figure 9.51 – Device remediation actions
The available remediation actions on a device, shown in Figure 9.51, include the following:
• Run Antivirus Scan: Initiate a Microsoft DefenderAntivirus (AV) scan (whether or not Defender AV is the active solution or not).
• Collect Investigation Package: Selecting this initiates data collection on the target device. The device must be online and connected to Microsoft 365 Defender for this action to take effect. Once completed, the resultant file (MDE_Investigation_Package.zip) contains core information about the device, including the following:
- Autoruns: Registry output of various startup registry keys
- Installed Programs: Text and CSV files containing registry information regarding installed programs
- Network connections: Output of various network statistics commands, including IP configuration, DNS cache, ARP table, active network connections, and firewall activity
- Prefetch files: File header information that is stored whenever a file is executed for the first time
- Processes: CSV listing of active processes
- Implementing and Managing Endpoint Protection by Using Microsoft Defender for Endpoint
- Scheduled Tasks: CSV listing of scheduled tasks
- Security Event Log: Export of the security event log
- Services: CSV listing of installed or configured services
- SMB Session: Summary of established Server Message Block (SMB) communications sessions with other hosts
- System Information: Text export of basic system information, including device name, operating system version, BIOS and processors, installed hotfixes, domain membership, locale data, and memory configuration
- Temp Directories: Contents of any identified temporary files directories
- Users and Groups: Lists of locally configured users, groups, and group memberships
- WdSupportLogs: Windows Defender support logs
- Forensics Collection Summary: List of the types of data collected as part of the Collect Information Package task, including the local commands used to gather the data
- Restrict App Execution: This invokes a protection mechanism that prevents applications not signed by Microsoft from running.
- Initiate Automated Investigation: Start a general-purpose automated investigation to look for any other potential issues. Any alerts generated on this device during the investigation will automatically be added to this investigation, as well as other instances of the same threats detected on other devices.
- Initiate Live Response Session: Launch a remote PowerShell session to the device to run additional scripts or gather additional data.
- Isolate Device: Immediately block all traffic on the device except to Microsoft 365 Defender. This is also sometimes referred to asContain Device.
- Ask Defender Experts: An additional available service, Microsoft 365 Defende Experts allows you to ask Microsoft security personnel to help provide context around threats. For more information on Threat Experts, see https://learn.microsoft.com/en-us/ microsoft-365/security/defender/onboarding-defender-experts-for-hunting.
- Download force release from isolation script: This script, executed locally on an isolated device, can be used to un-isolate a device not responding to Microsoft 365 Defender. The script is valid for 3 days, after which time, a new script must be generated to run on the device.
When executing the Collect Information Package option, you may need to navigate away from the view where it was activated. To avoid accidentally re-running the collection, you can use the Action center context menu item to see the results of pending actions (such as a collection file availablefor download).
