You can leverage device health and compliance data as part of a Conditional Access policy. In Figure 9.13, you can see that the Require device to be marked as compliant checkbox has been selected as a Grant access control:
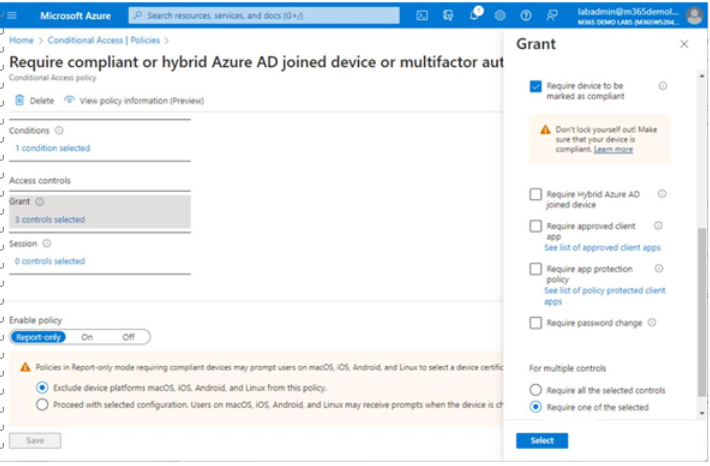
Figure 9.13 – Enabling device compliance as a requirement for Conditional Access policy
Devices are marked compliant using the integration between Intune and Defender for Endpoint to report on whether the device meets compliance standards (such as current antimalware software or no unresolved threats). For more information on configuring Conditional Access policies, refer to Chapter 6, Implementing and Managing Secure Access.
The final step for integration is onboarding devices to Defender to Endpoint. We’ll look at that next.
Onboarding Devices to Defender for Endpoint
Onboarding devices can take many forms, depending on both the type (mobile versus computer device) and the operating system (current versions of Windows, previous or legacy versions of Windows, Android, Linux, macOS, or iOS) . The latest Windows clients have the software built in and merely have to be instructed to connect to the Defender service, while others may require agents or client software to be installed.
Microsoft recommends using Intune as the deployment method, which typically requires newer devices and operating systems. This helps ensure that you’re using systems that are under current maintenance or support agreements and have security updates regularly published. Newer devices and operating systems are also able to take advantage of the latest advances in management tooling. You can also onboard using Intune, local scripts, Group Policy, or third-party management platforms that leverage the scripting or packages supplied by Microsoft. It is not supported, however, to re-package the MDE deployment as it may trigger tampering alerts.
Note
You’ll notice from the supported requirements that systems as far back as Windows 7, Android 8, and iOS 13 are supported. Many of those platforms, however, are out of vendor support and no longer receive security updates. Microsoft recommends using the latest supported operating system platforms and applications.
In this section, you’ll focus on using Intune to deploy MDE, but you’ll see some high-level information on other methods as well.
Onboarding Windows Devices
With Intune and Defender for Endpoint integration, onboarding Windows devices is relatively simple. After the connectivity between Intune and MDE is established, Intune can begin receiving the onboarding package configuration from Defender for Endpoint. Intune, in turn, uses a device configuration profile to deploy the configuration to Windows devices.
Onboarding with Intune
Microsoft’s preferred method for onboarding Defender for Endpoint is through Microsoft Intune. The integration between Intune, MDE, and the rest of the Microsoft 365 platform helps automate onboarding, configuration, and standardization across your organization.
If you have already configured the service-to -service integration between Intune and MDE, there’s nothing else to do. If you haven’t done that yet, turn a few pages back and read the Integrating Defender for Endpoint with Intune section earlier in this chapter.
The process of either hybrid-joining devices (via Azure AD Connect synchronization, signing in to a new device with an Entra ID identity, or using the Add a work or school account wizard) will onboard your device to Intune and Defender for Endpoint. You can view your device’s status by opening Accounts | Access work or school, as shown in Figure 9.14:
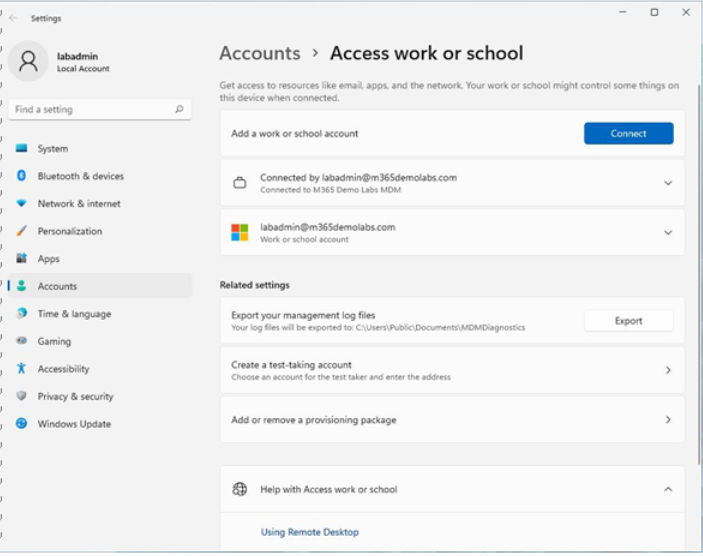
Figure 9.14 – Access work or school screen
You can also view your device’s status using the dsregcmd /status command, as shown in Figure 9.15:
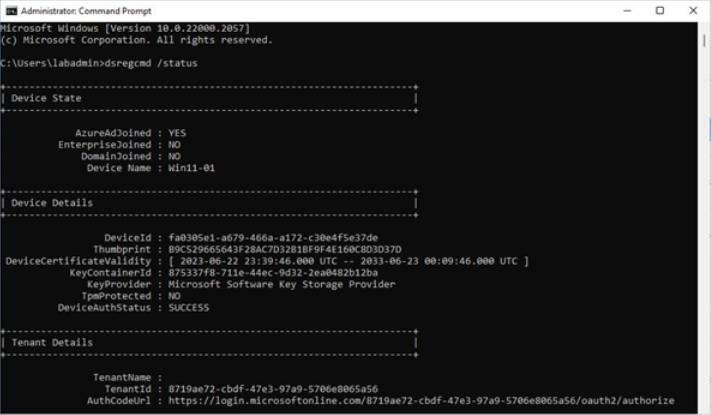
Figure 9.15 – Viewing device join status
Once you’ve onboarded to Intune in an environment with the service-to-service connection enabled, you’ll need to wait for the policy refresh cycle to configure the device.
